OnApp leverages the iptables and arptables applications on the hypervisor to secure the network of hypervisors. The following diagram shows two VMs connected to the Linux bridge which rth0 is also a member of.
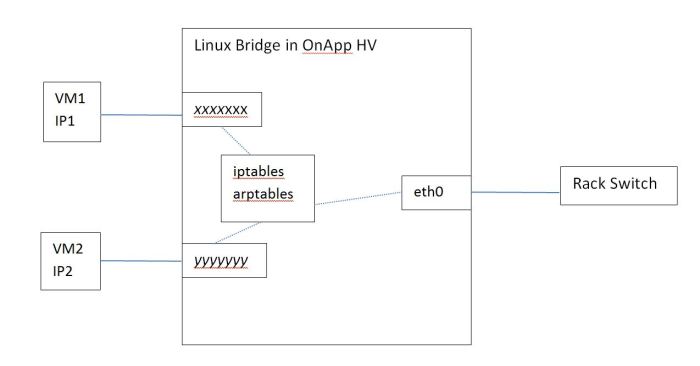
By default Onapp add rules to iptables and arptables in order to implement the following security and isolation goals at the Linux bridge level:
- Only packets with source IP1 can enter port xxxxx and can only exit from eth0 and the same for IP2 and port yyyyy.
# iptables -L FORWARD -vChain FORWARD (policy DROP 978M packets, 67G bytes)
pkts bytes target prot opt in out source destination
293K 184M ACCEPT all — any any IP1 anywhere PHYSDEV match –physdev-in xxxxxxx –physdev-out eth0
310K 128M xxxxxxx all — any any anywhere IP1 PHYSDEV match –physdev-out xxxxxxxx
- Packets with destination address IP1 can exit only from port xxxxx. A chain named xxxxx is created and client can add their own rules to control the incoming traffic to the VM at the hypervisor level.
Chain xxxxxxx (1 references)pkts bytes target prot opt in out source destination
6939K 6242M ACCEPT all — any any anywhere anywhere state RELATED,ESTABLISHED
4634 436K ACCEPT all — any any anywhere anywhere
- Only ARP replies with source address IP1 can enter port xxxxx
# arptables -L FORWARD -vChain FORWARD (policy DROP 22358 packets, 626K bytes)
-j ACCEPT -i any -o any –opcode Request , pcnt=3217M — bcnt=90G
-j ACCEPT -i eth0 -o any –opcode Reply , pcnt=3664K — bcnt=103M
-j ACCEPT -i xxxxxxxx -o any -s IP1 –opcode Reply , pcnt=14064 — bcnt=394K
These rules prevent packet sniffing considering that the VMs are on the same broadcast domain. Also prevents the VM from using any unauthorized IP, for example VM1 cannot use IP2.
The arptables rule prevents ARP spoofing.
If a client has a private VLAN and VM needs to act as gateway or VPN server we need to make some changes in iptables and arptables rules.

We assume that the IP range 192.168.0./24 has been used for private VLAN (ports xxxxx, zzzzzz etc.) We have to make two modifications to iptables and arptables rules.
# iptables -A FORWARD –src 192.168.0.0/24 -m physdev –physdev-out zzzzzz -j ACCEPT
This rule allows the exit from port zzzzzz in addition to default eth0.N
# arptables -A FORWARD -i zzzzzzz -s 192.168.0.0/24 –opcode Reply -j ACCEPT
This rule allows for VM2 to act as ARP proxy for the subnet 192.168.0.0/24. This rule is needed if we are configuring a layer 2 VPN server. After running above commands the following rules are appended to the end of FORWARD chain in iptables and arptables.
# iptables -L FORWARD -nv
Chain FORWARD (policy DROP 980M packets, 68G bytes)
pkts bytes target prot opt in out source destination
44 3223 ACCEPT all — * * 192.168.0.0/24 0.0.0.0/0 PHYSDEV match –physdev-out xxxxxxx
# arptables -L FORWARD -v
Chain FORWARD (policy DROP 22476 packets, 629K bytes)
-j ACCEPT -i xxxxxxxx -o any -s 192.168.0.0/24 –opcode Reply , pcnt=170 — bcnt=4760